Fake PDF editor tools are spreading infostealer malware via malicious ads & downloads.
Solis recently investigated an infostealer threat originating from user-downloaded Trojan PDF editor tools. Since dubbed TamperedChef, this malware demonstrates the importance of user awareness of the risks of downloading software from unapproved sources.
Most infections our Managed Services team investigated began with redirection from malicious advertisements displayed alongside search results. Purporting to offer free PDF utilities, these linked to malicious domains (most commonly fullpdf[.]com – since taken down), where the user would be prompted to download an MSI installer file (AppSuite-PDF.msi).
Upon execution, the installer wrote the Trojan application to a folder within the user directory (C:\Users\<user>\PDFEditor). However, the utility’s executable would also write node.exe and a JavaScript file to different directories within the AppData folder, along with a scheduled task containing a command designed to execute the script on a daily basis:
> "C:\Windows\system32\cmd.exe" /c start "" /min "C:\Users\\AppData\Roaming\ NodeJs\node.exe" "C:\Users\\AppData\ Local\TEMP\xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxxxxxxxx.js"
The scheduled task’s name usually began with “sys_component_health_”, followed by a long, random, GUID-style string. The JavaScript file name followed a similar random format.
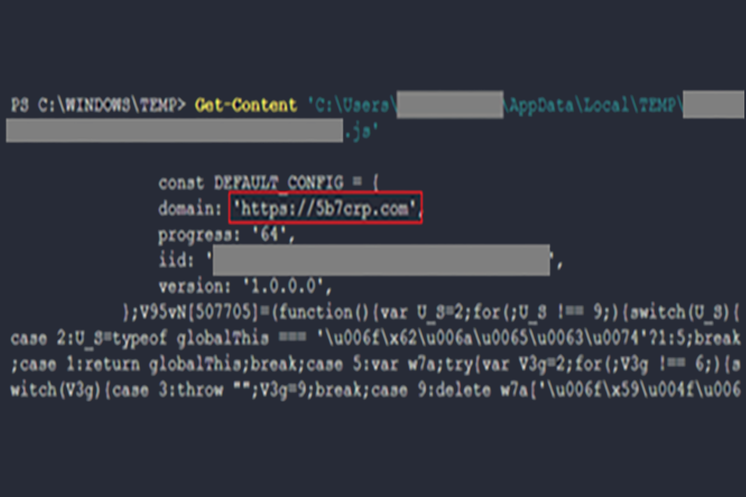
The contents of the script were highly obfuscated, but our analysis showed that the infostealer had capabilities that allowed it to collect and exfiltrate system information and browser data, potentially including credentials and cookies. A command and control domain was also visible inside each version of the script, and requests were observed upon execution.
The campaign capitalises on users requiring PDF editing functionality beyond the software made available by their organisations. User awareness training can help to encourage users to contact their IT teams if they require additional software, rather than searching for solutions online and downloading utilities from unapproved sources.
Solis developed custom detection content to intercept TamperedChef at the point of delivery for new infections, and to detect ongoing execution for infections already present at the time our endpoint detection and response tooling is deployed. Our Managed Detection and Response for Endpoint service fully remediates associated artefacts on customer endpoints.
Solis MDR for Endpoint provides 24/7 monitoring, investigation, and remediation of cyber security threats to your organisation’s workstations, laptops, and servers. Contact our team today at enquiries.uk@solissecurity.com to discuss how we can protect your business.



