Think MFA Keeps You Safe? Think Again.
As an incident responder, this is a statement I hear daily regarding an account being compromised. Unfortunately, today MFA alone is not a silver bullet to ensure protection, as 73% of incidents investigated show. Since the day technology became widely available to us all, it has been a constant "cat and mouse" game between the "good guys" and "bad guys". As security professionals and software developers advance methods to bolster applications, threat actors are also working in the background. They find vulnerabilities within those processes that they can leverage to gain access, steal data, or worse, encrypt those systems.
One of the most common techniques observed by Solis as a method to bypass MFA in business email compromises is Adversary-in-the-Middle (AiTM) phishing. Phishing emails have been identified as the root cause for 86% of the email compromise incidents investigated by Solis in the first six months of 2025. Traditionally, phishing emails were thought to steal the target's username and password. As organizations began to roll out MFA, just a username and password have become increasingly less significant. Consequently, AiTM phishing attacks have become more prevalent.
So, what is AiTM phishing, and how does it work? AiTM phishing is a more sophisticated type of cyberattack where the threat actor can intercept the communication between a target user and a legitimate website. In the scenario discussed in this post, it involves MFA bypass for email clients. The threat actor would use the phishing email to steal the session cookies. This will then trick the email client into not prompting the threat actor for MFA, as it would think MFA has already taken place a short period before. Consequently, the threat actor is granted free rein within the compromised mailbox.
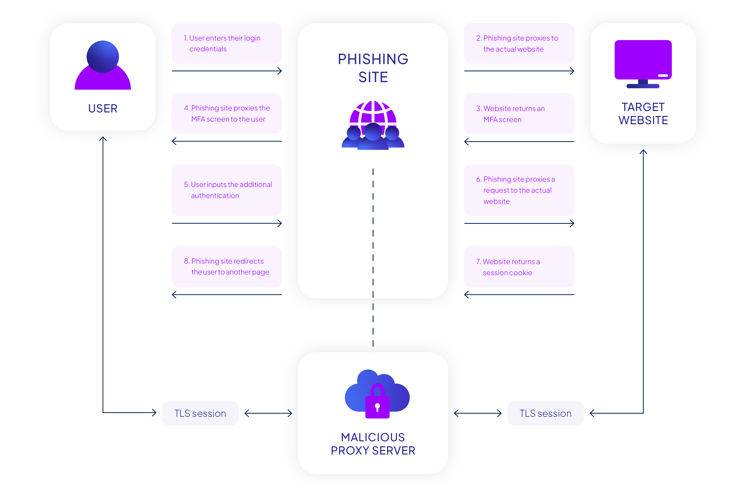
In the instances observed by Solis, the threat actor will use AiTM by working as a proxy between the targeted victim and the target site. Due to Microsoft being the most popular platform for businesses (94% of email compromise incidents investigated by Solis in 2025 used Microsoft 365 as their email tenant), threat actors often impersonate the Microsoft login screen by setting up a spoof page.
In this case, this will be referred to as the proxy site. Threat actors tailor the phishing email to make the recipient as likely as possible to click on the malicious link.
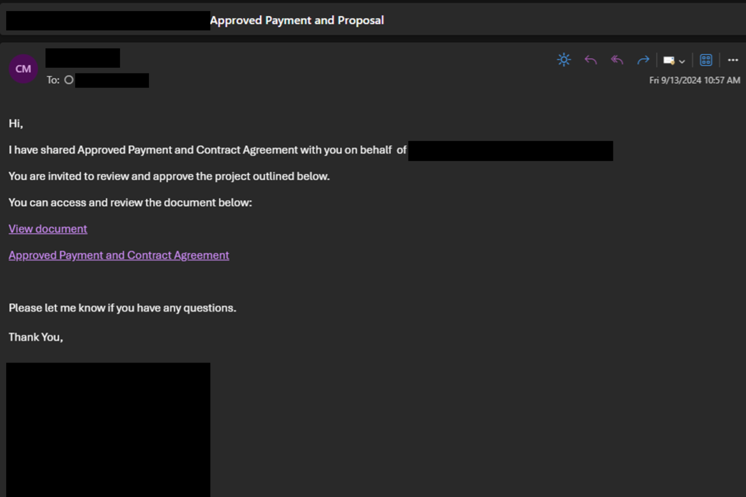
In the example below, the threat actor had leveraged a compromised account and attempted to get the recipient to click the hyperlinked text.
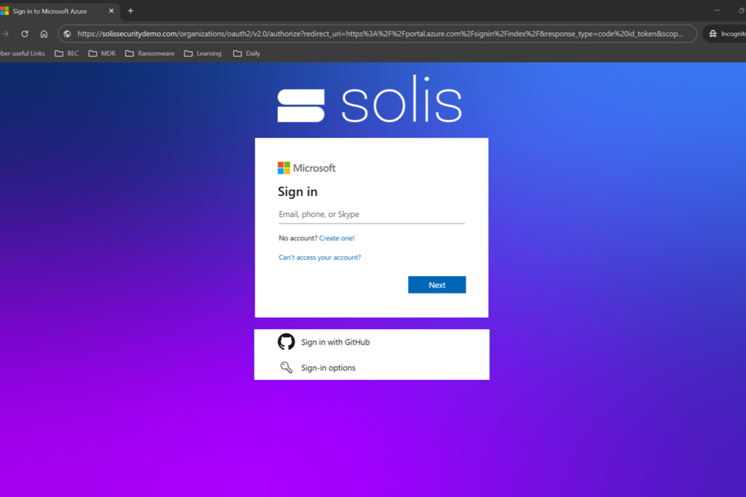
The once simple but effective step of personalising your sign-in page has also been proven to be insufficient by threat actors too, as is displayed within the example screenshot below:
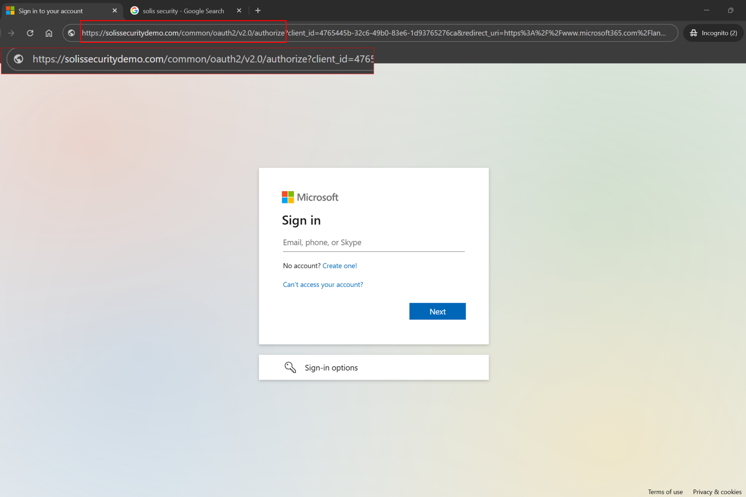
The only giveaway would be the URL as highlighted below:
Once the user has entered their login credentials, if MFA is enabled for the user, the spoof page will also prompt them to enter the code requested by Microsoft to gain access. Once all of this has been completed, the user will usually be greeted with a blank page. At this point, most users would disregard their actions and continue with their workday, believing it’s a glitch. This will then allow the threat actor to use the stolen credentials and deceive Microsoft into not prompting them for MFA. Once in the account, the threat actor will set up their device within the authenticator for persistence.
This all sounds terrible, so now that we know MFA isn’t enough, what can we do to better secure our email accounts? Solis will make the following recommendations to reduce the likelihood of an account compromise on the back of a phishing email:
• Switching to phishing-resistant forms of MFA: Switching from the standard Microsoft code-based MFA to a FIDO2 key could greatly improve your organization's security and resilience to AiTM phishing attempts. FIDO2 keys are physical keys that generate unique codes for every sign-in. Due to the FIDO2 keys' zero-trust functionality, a session cookie wouldn’t bypass the requirement for the code. (should I mention some of the negatives?)
• Certificate-based authentication: Although a FIDO2 key is a form of certificate-based authentication, other methods could also be used, such as a smart card. This physical form of additional authentication would strengthen your organization against unauthorized access to an account within your tenant, as the credentials stolen from the phish would prove to be redundant.
• Conditional access: The proper configuration of your email tenant can be the easiest and most cost-effective method to secure your email environment against phishing emails. The conditional access rule can be set up to block sign-ins outside of listed trusted locations (i.e., offices), which would greatly reduce the likelihood of a threat actor being able to access the email environment. Another conditional access rule that can be set up would be to deny access to any device that isn’t already registered within your environment.
• Managed detection and response / Improved monitoring: The use of an external managed detection and response (MDR) team that monitors the activity of your email tenant could greatly reduce the impact of a phishing email compromise. MDR teams would monitor your environment against suspicious sign-ins and activity.
• User training: You know, we had to add it. No matter how many security controls you have in place, social engineering of a genuine user can allow the threat actor to get into your organization's environment. Ensuring users are trained to avoid interacting with phishing emails or social engineering attempts.



